Introduction
It is always important to protect your enterprise’s sensitive data. The Windows access control list (ACL) only can do the partial job. Because you can’t set the ACL to the specific processes, you also can’t control the file access dynamically in your application. The EaseFilter File Control Filter Driver SDK can provide you a comprehensive file security solution. So you can authorize or deny the file access to the specific users or the processes. The EaseFilter allows you to monitor or control the file I/O activities in file system level in real time. So you can prevent your sensitive files from being accessed by unauthorized users or processes.
Understand The File Control Filter Driver
The EaseFilter driver is a kernel-mode component that runs as part of the Windows executive above the file system. The file system filter driver can intercept requests targeted at a file system or another file system filter driver. By intercepting the request before it reaches its intended target. The file control filter driver can extend or replace functionality provided by the original target of the request. You can log, monitor, modify, or prevent the I/O operations for one or more file systems with the filter driver.
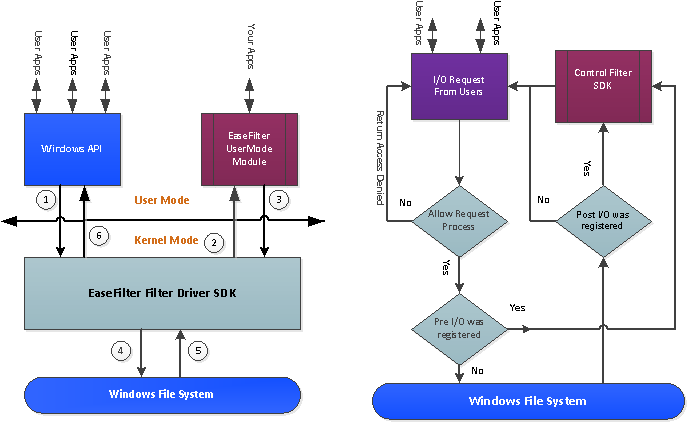
How To Control The File Access With The Filter Driver
The EaseFilter control filter driver can intercept the file I/O before it goes down to the file system or after it returned from the file system. You can deny the file access in the pre file I/O operations based on the filter rule policies. It meant that the EaseFilter can complete and return the file I/O without going down to the file system. Also you can modify the I/O data before it goes down to the file system or after it returned from the file system.
Block the file I/O operations in pre-IO
With the file system filter driver, you can prevent your files from being changed, you can block the file operations before it goes down to the file system, normally we called it pre-IO. For example if you want to block the file creation, file deletion, file written and file rename, then you can complete file operation with access denied status before it goes down to the file system.
With the filter rule setting, you can setup the file access policies easily, you can setup the access rights to the specific users or processes. So you can authorize the file access to the specific users or processes, or deny the file access to the specific users or processes.
Modify the file I/O data in pre-IO or post-IO
You can modify the file I/O data in pre-IO or post-IO. To modify the file I/O data, you must be an advanced user who understand the file I/O data structure, or you will corrupt a file. For example you can replace the write data in the pre-IO, the file encryption is a very good example. You can replace the read data in the post-IO, the file decryption is a very good example too.
How to setup the zero-trust file access filter rule
It is simple to implement the zero-trust file security solution with EaseFilter SDK. Zero-trust meant all users or processes can’t access the files by default. In EaseFilter file control SDK, you just need to setup a file control filter rule with zero access right, then the zero-trust file protection is enabled.
Authorize the file access to the specific users or processes
With the zero-trust solution, by default all users or process are in the blacklisting. No one can’t access your files if you don’t authorize the user or process to access the files. It can prevent the attack from the malicious software.
You can create a whitelisting users or processes by adding the access rights to the specific users or processes. So you can authorize the file access to the approved users or processes.
Hide the files with the filter mask
With the EaseFilter SDK, you can setup the filter rule to hide the files based on the file filter mask. You can hide the files for the specific users or processes. So the unauthorized users or processes can’t see your sensitive files.
Reparse the file open with the filter mask
With the EaseFilter SDK, you can setup the filter rule to reparse the files open to another folders. With the reparse file filter rule, it allows you to open the files from folder1 to folder2.
How To Implement The Security Application With The EaseFilter File Security SDK
The EaseFilter File Security SDK provides a rich set of the APIs for the applications to manage the filter driver’s functionalities. You can implement the security application with the EaseFilter file system filter driver SDK easily. You can run your application as console application or run as a Windows service.
The EaseFilter SDK provides the APIs similar to the Win32 APIs, all programming languages which can use the Windows Win32 API can use the EaseFilter SDK. Currently the EaseFilter SDK provides the C++/C# demo source code, so you can integrate the EaseFilter SDK into the Windows application with C++/C# demo source code easily.
The following C# example creates a filter rule to protect the directory specified at run time. The filter rule was set to protect the folder against the file being renamed, deleted, written. The component is registered with the create and delete IO callback event in the directory. If a file was opened or deleted, the event will be triggered, you can allow or block the IO in the event. To understand the more functionalities of the EaseFilter SDK, you can reference the FileProtector example.
using System;
using EaseFilter.FilterControl;
namespace FileProtectorConsole
{
class Program
{
static FilterControl filterControl = new FilterControl();
static void Main(string[] args)
{
string lastError = string.Empty;
string licenseKey = "Email us to request a trial key: info@easefilter.com";
FilterAPI.FilterType filterType = FilterAPI.FilterType.MONITOR_FILTER|FilterAPI.FilterType.CONTROL_FILTER
|FilterAPI.FilterType.PROCESS_FILTER|FilterAPI.FilterType.REGISTRY_FILTER|FilterAPI.FilterType.ENCRYPTION_FILTER;
int serviceThreads = 5;
int connectionTimeOut = 10; //seconds
try
{
//copy the right Dlls to the current folder.
Utils.CopyOSPlatformDependentFiles(ref lastError);
if (!filterControl.StartFilter(filterType, serviceThreads, connectionTimeOut, licenseKey, ref lastError))
{
Console.WriteLine("Start Filter Service failed with error:" + lastError);
return;
}
//the watch path can use wildcard to be the file path filter mask.i.e. '*.txt' only monitor text file.
string watchPath = "c:\\test\\*";
if (args.Length > 0)
{
watchPath = args[0];
}
//create a file protector filter rule, every filter rule must have the unique watch path.
FileFilter fileProtectorFilter = new FileFilter(watchPath);
//configure the access right for the protected folder
//prevent the file from being deleted.
fileProtectorFilter.EnableDeleteFile = false;
//prevent the file from being renamed.
fileProtectorFilter.EnableRenameOrMoveFile = false;
//prevent the file from being written.
fileProtectorFilter.EnableWriteToFile = false;
//authorize process with full access right
fileProtectorFilter.ProcessNameAccessRightList.Add("notepad.exe", FilterAPI.ALLOW_MAX_RIGHT_ACCESS);
//you can enable/disalbe more access right by setting the properties of the fileProtectorFilter.
//Filter the callback file IO events, here get callback before the file was opened/created, and file was deleted.
fileProtectorFilter.ControlFileIOEventFilter = (ulong)(ControlFileIOEvents.OnPreFileCreate | ControlFileIOEvents.OnPreDeleteFile);
fileProtectorFilter.OnPreCreateFile += OnPreCreateFile;
fileProtectorFilter.OnPreDeleteFile += OnPreDeleteFile;
filterControl.AddFilter(fileProtectorFilter);
if (!filterControl.SendConfigSettingsToFilter(ref lastError))
{
Console.WriteLine("SendConfigSettingsToFilter failed." + lastError);
return;
}
Console.WriteLine("Start filter service succeeded.");
// Wait for the user to quit the program.
Console.WriteLine("Press 'q' to quit the sample.");
while (Console.Read() != 'q') ;
filterControl.StopFilter();
}
catch (Exception ex)
{
Console.WriteLine("Start filter service failed with error:" + ex.Message);
}
}
///
/// Fires this event before the file was opened.
///
static void OnPreCreateFile(object sender, FileCreateEventArgs e)
{
Console.WriteLine("OnPreCreateFile:" + e.FileName + ",userName:" + e.UserName + ",processName:" + e.ProcessName);
//you can block the file open here by returning below status.
e.ReturnStatus = NtStatus.Status.AccessDenied;
}
///
/// Fires this event before the file was deleted.
///
static void OnPreDeleteFile(object sender, FileIOEventArgs e)
{
Console.WriteLine("OnPreDeleteFile:" + e.FileName + ",userName:" + e.UserName + ",processName:" + e.ProcessName);
//you can block the file being deleted here by returning below status.
e.ReturnStatus = NtStatus.Status.AccessDenied;
}
}
}